From South Africa. Posted May 22, 2011. Thanks a million. Okay, after repeated downloads of parts 3 and 5, they consistently have the same MD5 hash. That MD5 hash is NOT the one you've posted Doofdilla. This means that the files being served from the server to my IP address must be corrupted on the server. MD5 file hashes uniquely identify file content and can be used to check whether file content is identical. In PowerShell 5, there is a new cmdlet that creates the hashes for you. The code below looks for all PowerShell scripts in your user profile, and generates MD5 hashes for each file.

Frequently Asked Questions: Basic concepts
This article helps you verify and troubleshoot ExpressRoute connectivity. ExpressRoute extends an on-premises network into the Microsoft cloud over a private connection that is commonly facilitated by a connectivity provider. ExpressRoute connectivity traditionally involves three distinct network zones, as follows: Customer Network. Step 3: Use Copy to Clipboard functionality to copy the generated MD5 hash. What is MD5 HASH? MD5 is a message-digest algorithm. It's developed by Ronal Rivest in 1991 to make it more prominent than MD4. MD5 Hash string is usually represented as a hexadecimal number of 32 digits. MD5 is widely discussed and widespread historical use. MD5 is known as well known hashing algorithm, used for purposes such as storing information and using it as a checksum to check whether the data is the same. It applies several calculations on a given string, such as the shifting and adding of bits, which results in a 128-bit hash.
The MD5 hash also known as checksum for a file is a 128-bit value, something like a fingerprint of the file. There is a very small possibility of getting two identical hashes of two different files. This feature can be useful both for comparing the files and their integrity control.
Let us imagine a situation that will help to understand how the MD5 hash works.
Alice and Bob have two similar huge files. How do we know that they are different without sending them to each other? We simply have to calculate the MD5 hashes of these files and compare them.
Act now, and experience the MD5 hash checker utility for yourself, control your data! Download the MD5 hash checker now!
You can learn how to use it from the Online Help or by visiting the main page.
MD5 Hash Properties
The MD5 hash consists of a small amount of binary data, typically no more than 128 bits. All hash values share the following properties:
Hash length
The length of the hash value is determined by the type of the used algorithm, and its length does not depend on the size of the file. The most common hash value lengths are either 128 or 160 bits.
Non-discoverability
Every pair of nonidentical files will translate into a completely different hash value, even if the two files differ only by a single bit. Using today's technology, it is not possible to discover a pair of files that translate to the same hash value.
Repeatability
Each time a particular file is hashed using the same algorithm, the exact same hash value will be produced.
Irreversibility
All hashing algorithms are one-way. Given a checksum value, it is infeasible to discover the password. In fact, none of the properties of the original message can be determined given the checksum value alone.
The algorithm was invented by:
Professor Ronald L. Rivest (born 1947, Schenectady, New York) is a cryptographer, and is the Viterbi Professor of Computer Science at MIT's Department of Electrical Engineering and Computer Science. He is most celebrated for his work on public-key encryption with Len Adleman and Adi Shamir, specifically the RSA algorithm, for which they won the 2002 ACM Turing Award.
Calculate and change the MD5 hash for files
What's new in MD5 Hasher 1.0:
- Multi Threading support so no more hanging while hashing the +700MB files
As the name implies, MD5 Hasher is a program that allows you to find out the MD5 checksum of a file. It can be seamlessly handled, even by inexperienced users.
This is a portable software application, so installing MD5 Hasher is not required. In other words, you can save the tool to an external device (like a USB flash drive) and directly run the executable file on any computer.
Therefore, you can always carry MD5 Hasher with you when you're on the move. Plus, no items are left over in the Windows Registry or on the hard drive after deleting the tool.
The interface of the utility is based on a standard window with an uncomplicated layout. Files can be imported into the list by using the file browser, and you can add as many files as you want, since batch processing is supported.
The file queue provides the name, MD5 signature and location of each entry. So, you can select any two items from the queue and compare their MD5 checksums. MD5 Hasher also integrates a function to change the MD5 signature of one or more selected files (make sure to tick their boxes).
The tool runs on a very low amount of CPU and system memory, and has a good response time. The 'drag and drop' method is functional as long as you do not run the program with administrative rights. Other than that, MD5 Hasher's features can be effortlessly figured out.
Filed under
MD5 Hasher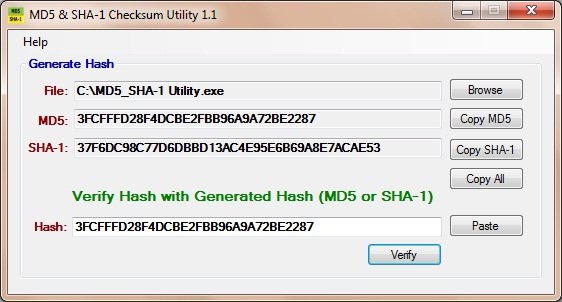 was reviewed by Elena Opris
was reviewed by Elena OprisMD5 Hasher 1.0
add to watchlistsend us an update- runs on:
- Windows 7
Windows Vista
Windows XP
Windows 2K - file size:
- 472 KB
- filename:
- MD5 Hasher 1.0.zip
- main category:
- Security
- developer:
Md5 Hash Regex
top alternatives FREE

Md5 Hasher
top alternatives PAID